You must either remove the offending using directive or delete the entire file (if you don’t need the stub Class). I talked about how to download and install Visual Studio in the last article. Fast-moving and evolving game-play code should be stored as source code in the Unity project. This is useful when you are distributing your code but don’t want to give away the source.
- If you want to search for all the three options, then check all the checkboxes.
- The only way to do that would be to try to run the Window version of Wireshark under Wine.
- On rare occasions, programs such as AutoCAD can become corrupted and require you to delete one or more of these folders.
If the subclass definition has a separate_fields_ variable, the fields specified in this are appended to the fields of the base class. _anonymous_¶An optional sequence that lists the names of unnamed fields._anonymous_ must be already defined when _fields_ is assigned, otherwise it will have no effect. Value, which contains success or error information for a function or method call. The constructor accepts an optional integer initializer. Tuple; it must return an object that can be used as a function call parameter. Arguments is a tuple containing the parameters originally passed to the function call, this allows specializing the behavior on the arguments used. This allows defining adapters that can adapt custom objects as function parameters.
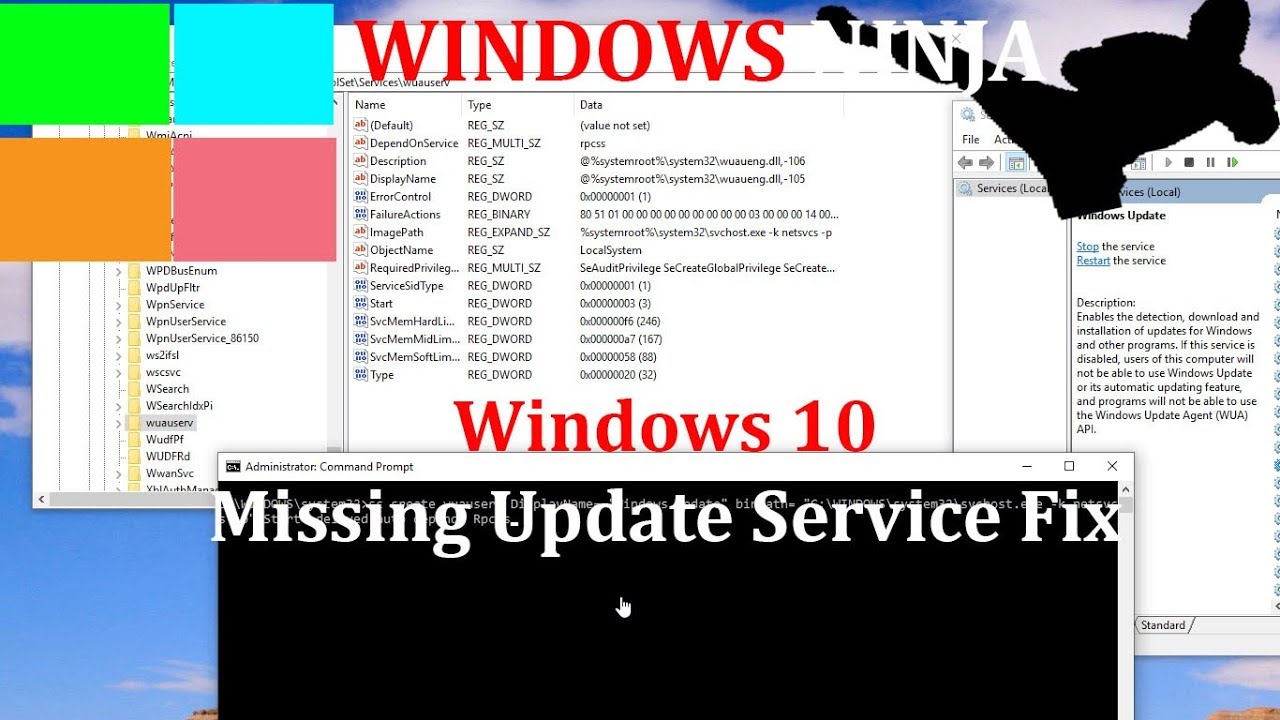
Explaining Straightforward Solutions In Dll Errors
For example, the path Explorer\Advanced would be in a string somewhere. We ntdll.dll may revise this Privacy Notice through an updated posting. We will identify the effective date of the revision in the posting. Often, updates are made to provide greater clarity or to comply with changes in regulatory requirements. Continued use of the site after the effective date of a posted revision evidences acceptance.
Working around the limitations of DLLs is probably more practical. They can be loaded into the memory space of other programs, where the functions can be executed and the data may be accessed. This loading takes place at runtime – either when the program starts, or when the program explicitly requests it via aLoadLibrary call or dlopencall .
- This is also useful for editing malicious startup items such as rogueware and ransomware.
- When you build a DLL with GCC, all functions, classes, and data are exported by default.
- The program only cares that it called that write fiction and it returned success.
Using it all the time will make your Windows not remain updated and you can be more likely to get a malicious attack while the overall performance will also have a decrease. By now, you’d have learned to set a metered connection in Windows 10. And if you follow the steps oppositely you would know how to turn off metered connection Windows 10. A metered connection is extremely safe and gives no harm to the operating system. It is more secure from malicious or malware activity. Metered connection carefully turns the existing connection and tracks the record of how much data you have consumed while using the internet to avoid expiring the plan with any notification.
A Spotlight On Simple Solutions For Dll Errors
Microsoft’s product keys typically only work once, but hackers sometimes find workarounds to use the same key on multiple PCs. It would be best to have a valid product key or a digital license to get a free upgrade. When you purchase an operating system from Microsoft or any retailer, it comes with a product key to unlock it. It’s printed and included in the packaging, emailed to you, or stored in the cloud, which is usually the case for system builders.
